Description
This article describes how to setup both ADFS and FortiGAte for SAML SSO for web mode SSL VPN with FortiGate acting as SP.
ADFS or Active Directory Federation Service is a feature which needs to install on AD server separately. Its main purpose is to provide Windows users with Single Sign-On (SSO) access.
Solution
Configuration On Fortigate.
# config user saml
edit “adfs”
set entity-id “https://10.5.27.2:10443/remote/saml/metadata/”
set single-sign-on-url “https://10.5.27.2:10443/remote/saml/login?”
set single-logout-url “https://10.5.27.2:10443/remote/saml/logout/”
set idp-entity-id “http://adfs.test.lab/adfs/services/trust”
set idp-single-sign-on-url “https://adfs.test.lab/adfs/ls/”
set idp-single-logout-url “https://adfs.test.lab/adfs/oauth2/logout”
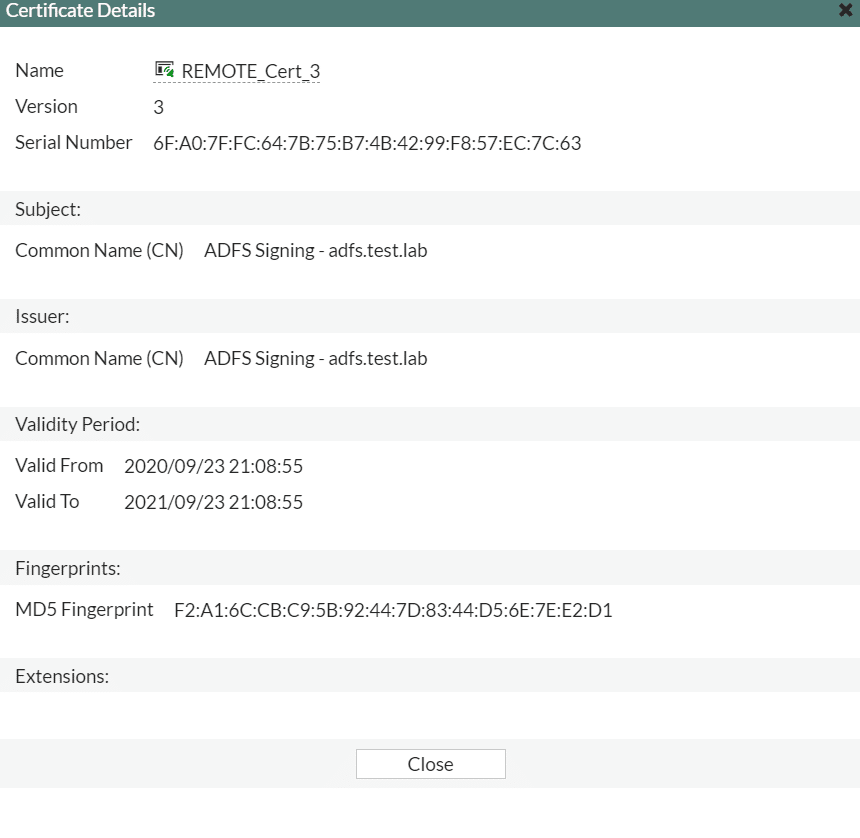
set idp-cert “REMOTE_Cert_3”
set user-name “username”
next
end
Configuration On ADFS:
1) Open ADFS from Server Manager -> Tools -> AD FS Management and navigate to Relying Party Trusts and Add Relying Party Trust.
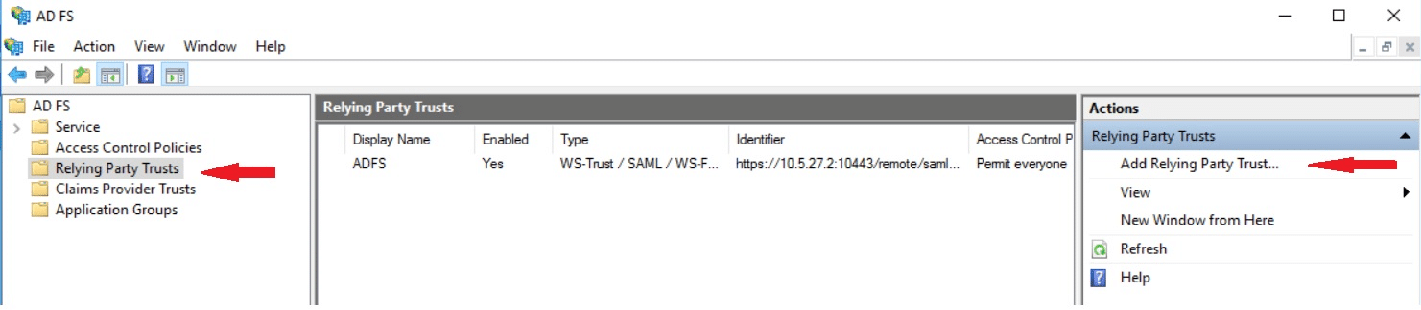
2) This will lead to a wizard where we have to provide all the information. In the Welcome page select ‘Claims aware’ and select ‘Start’.
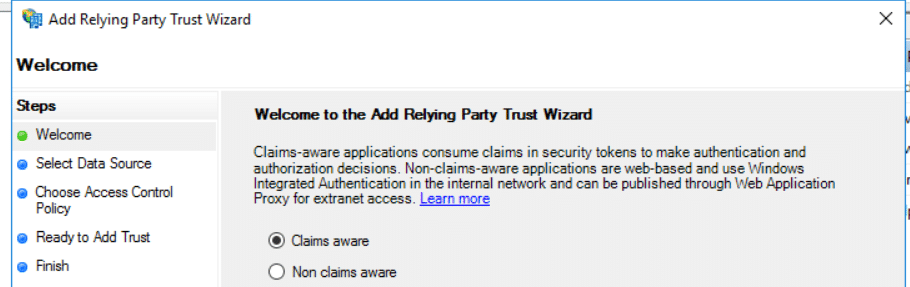
3) In the second page, there are three options provided. Choose the below shown option and select ‘Next’.
4) In the next page give any display of your choice and select ‘Next’.5) On this page just select ‘Next’ without making any changes.6) On ‘Configure URL’ Section. Enable SAML 2.0 option here and enter the Metadata URL from the FortiGate.
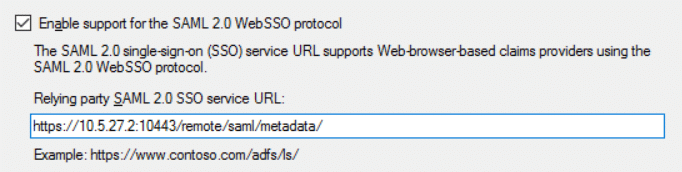
7) In this page add the identifier. The same metadata URL would be added as Identifier. select ‘Add’ after inserting the URL and then select ‘Next’.
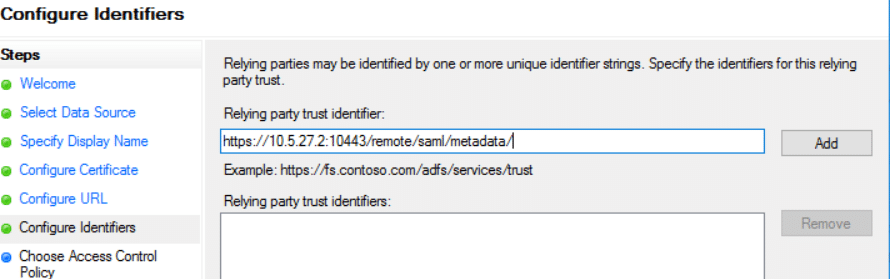
8) In the Access Control policy page, provide access to everyone. It is also possible to choose MFA options if enabled.
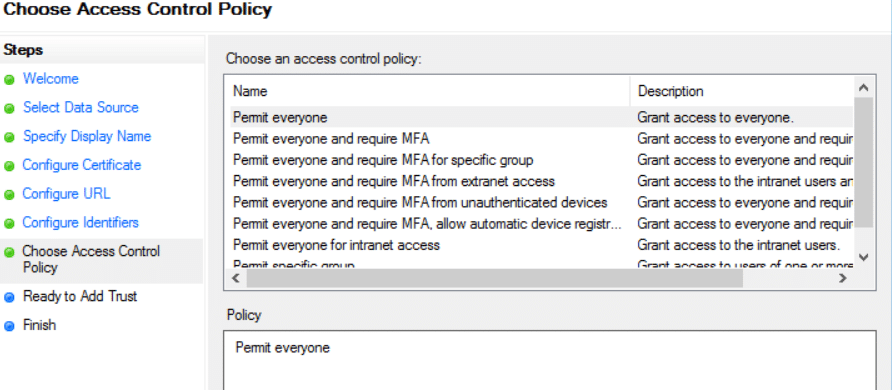
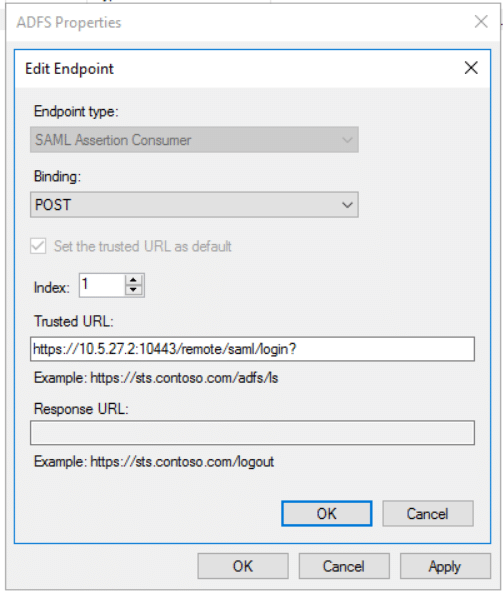
9) In the next page select ‘Next’ and ‘Finish’ to close the wizard.10) There are some more configuration required in the ADFS. Select on the newly created Relying party to edit. Go to Endpoint Tab. There will be only one URL configured. Edit the same like below and insert the login URL. Set the index to 1 and insert the login URL from the FGT and select ‘OK’.
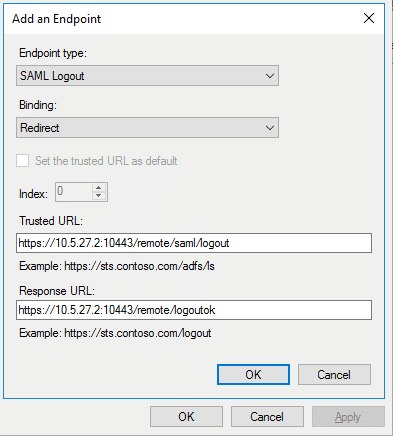
11) In the same Endpoint tab add another URL. Select ‘Add SAML’ and add the parameters as below. Once done save the changes and Apply. Close the editing after saving.
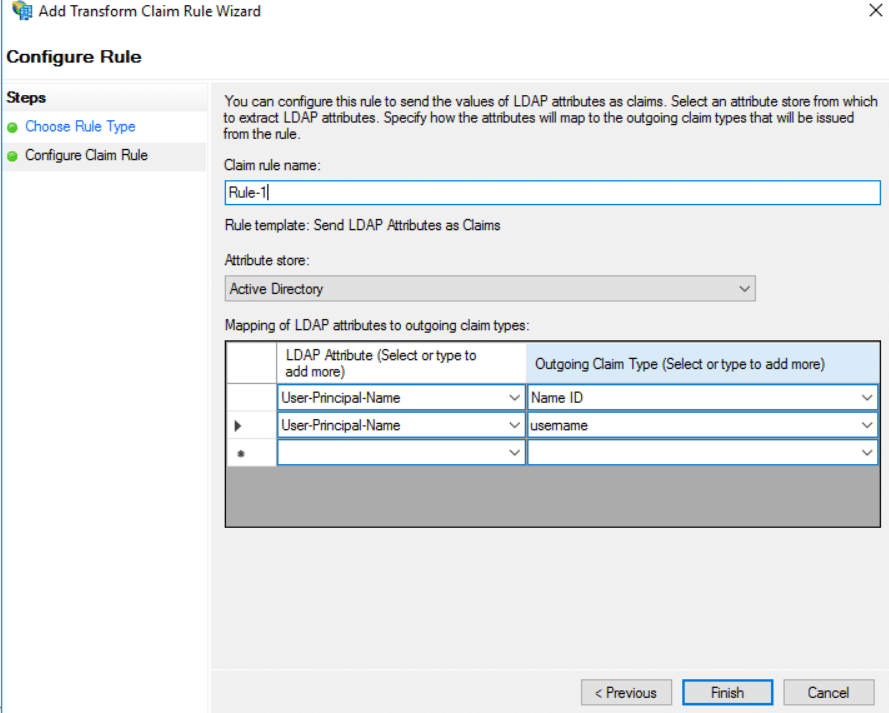
12) Now, select the Relying Party name which was created and select Edit Claim Issuance Policy. Once open, select ‘Add Rule’. Select the below option in the new wizard and select ‘Next’.
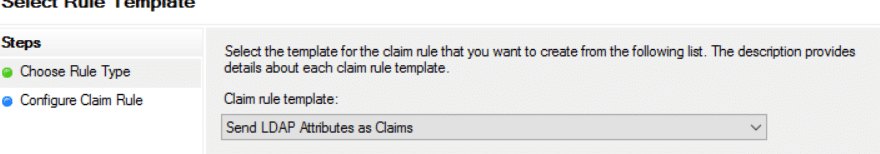
13) Configure the Claim Rule as below and select ‘Finish’ and ‘Apply’ once done.
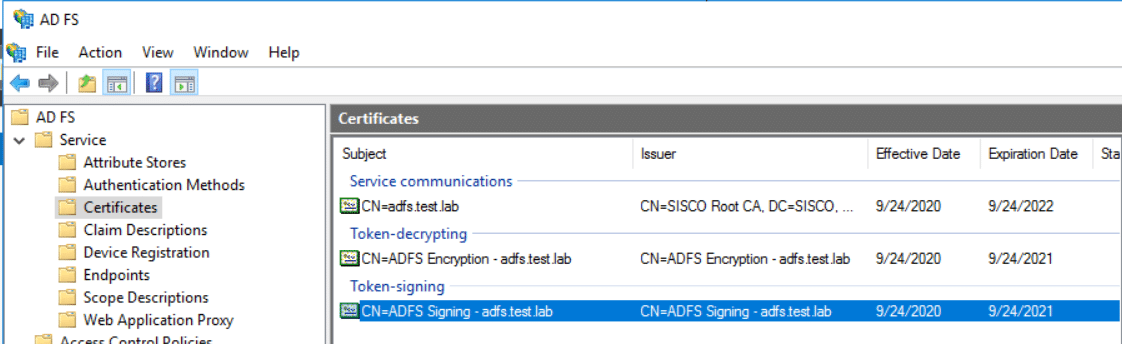
ADFS or IDP Information needed to configure in FGT.1) Certificate Download Path:Under ADFS Management, navigate to the below shown path to download the certificate. Make sure to download the certificate mentioned under ‘Token-signing’ and install it in the FortiGate.
It will be installed as Remote certificate in the FortiGate.
2) IDP sign-in and sign-out URL and IDP-entity URL can be found in the below URL.Open the URl in Google Chrome or Firefox and an xml file will be downloaded. Open the file and search for ‘entity’ and copy that URL. Search for ‘SingleSignOnService Location’ for IDP single sign-on URL. The same URL can be used for IDP single sign-out URL.The firewall policy and VPN configuration will be done as usual. The user group configuration will be as below:# config user groupedit “adfs-grp”set member “adfs”nextendTesting SSL VPN Web-mode:1) Enter the SSL VPN URL in the browser and select Single Sign-On
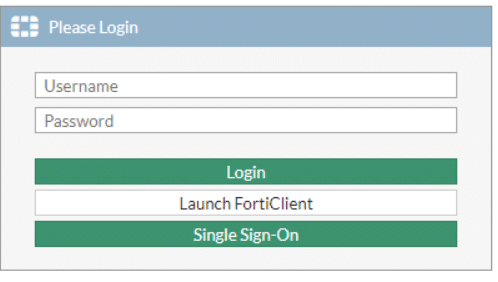
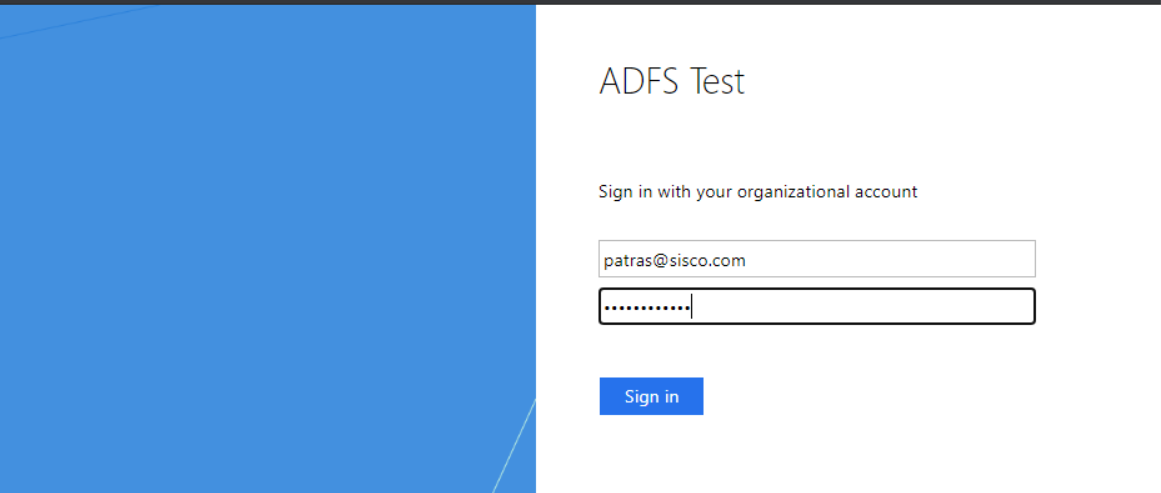
2) Insert AD credential and it will redirect to SSL Web Portal page.
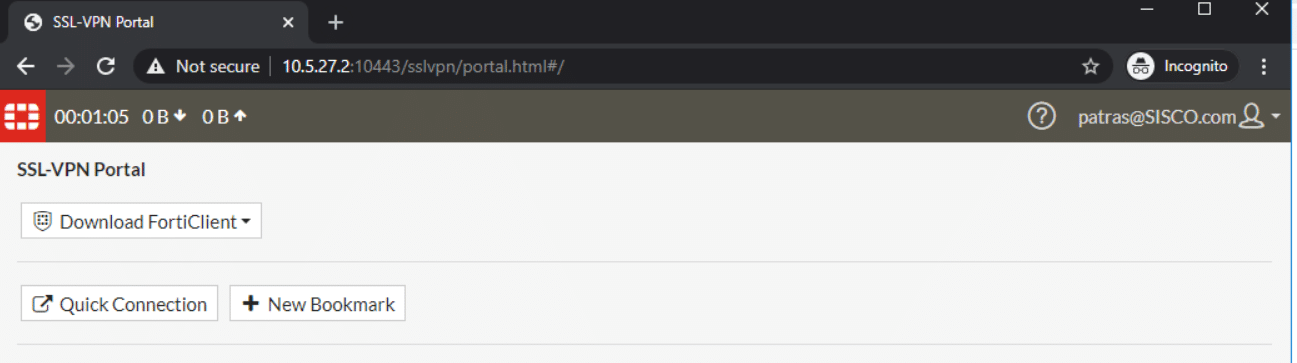
ion-kvm02 # get vpn ssl monitorSSL VPN Login Users:Index User Group Auth Type Timeout From HTTP in/out HTTPS in/out0 [email protected] adfs-grp 256(1) 215 10.220.6.107 0/0 0/0SSL VPN sessions:Index User Group Source IP Duration I/O Bytes Tunnel/Dest IP