Source: https://msendpointmgr.com/2020/09/23/bring-azure-ad-pim-and-intune-roles-together/
Microsoft Intune comes with a set of roles for role based access controls. The issue has been that these roles could only be assigned as permanent roles on a users or a group. Now with a new feature in Azure AD that gives us management capabilities for privileged access Azure AD Groups we can mitigate on this missing capability with Intune roles. In this post we will go through the steps needed to have Azure AD PIM control on any of the built-in or custom roles in Intune.
Requirement for this setup up is that you have Azure AD Premium P2 license and you have onboarded to Azure AD Privileged Identity Management.
The steps we need to get this working is as follows:
Role Assignable Group
Why do we need to have a special group type for this you ask. This group type is meant to be used for assigning users to Azure AD Roles, and only Global Admins and Privileged role admins can manage these groups. It can be delegated with assigning group owners if needed. The caveat is that a single Azure AD Tenant can have a maximum of 200 role assignable groups. The other reason is that we are only able to bring role assignable groups into PIM.
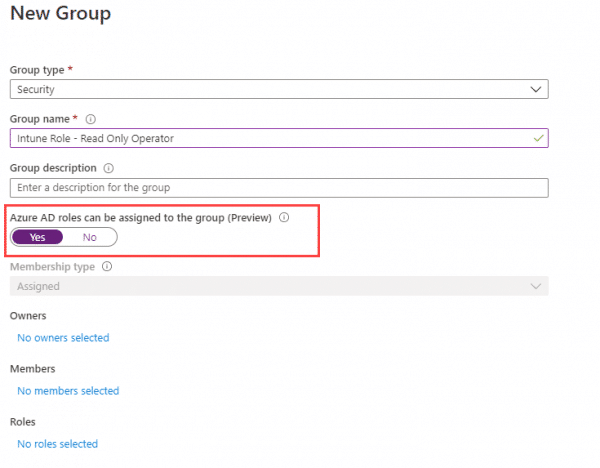
Go into AzureAD and create a new group and select Yes Azure AD roles can be assigned to the group. (This can not be changed later)
Do not add any members or roles to the group at this stage.
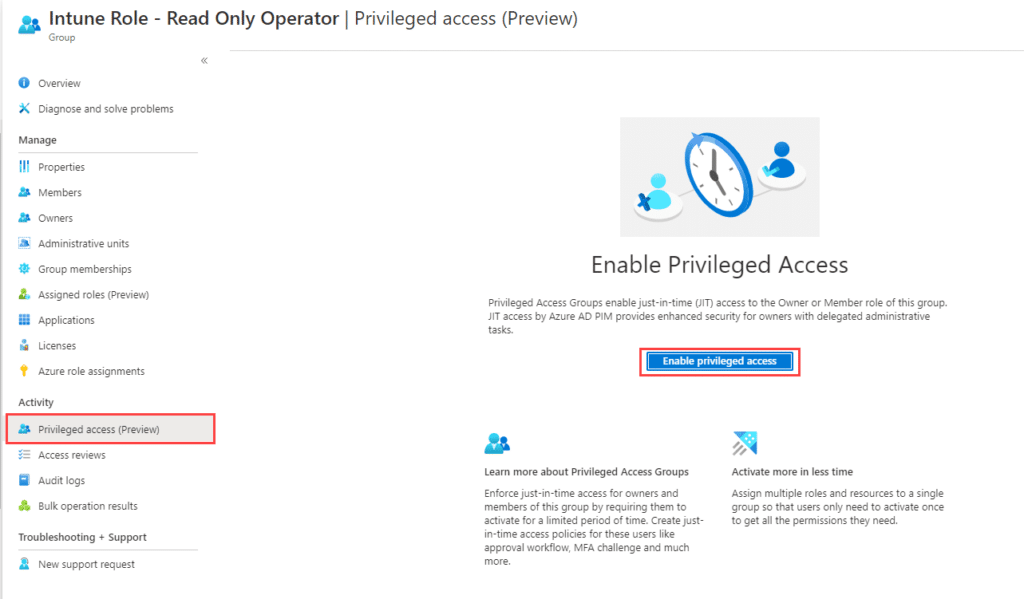
Bring the group into Privileged Identity Management (PIM)
Now that we have our group we need to bring this group into PIM. We do that by open up the group we created in Azure AD and go to Activity -> Privileged access (preview)
You will be redirected to this step after onboarding is completed.
Assign the group to the role in Intune
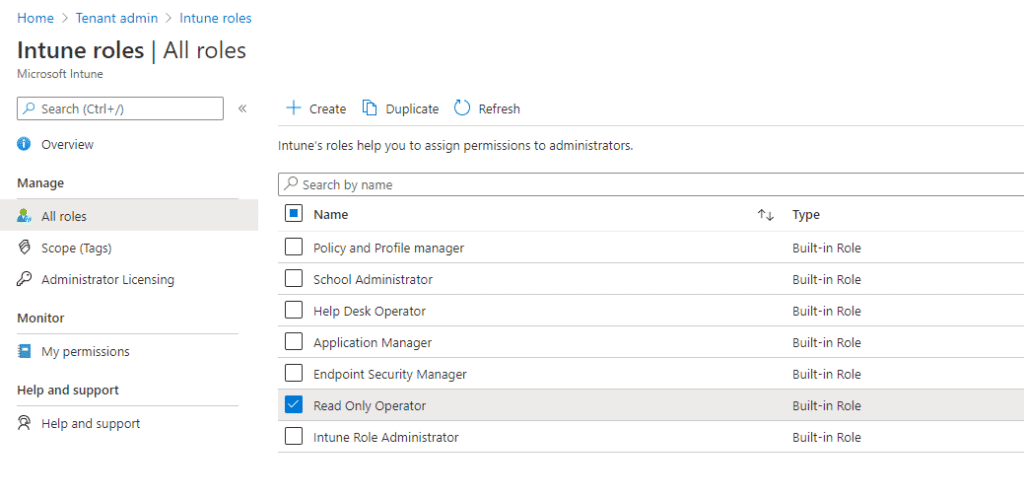
Now we have the group ready for our Intune built-in role. This can not be assigned from Azure AD so go to https://endpoint.microsoft.com and select Tenant Administration – Roles
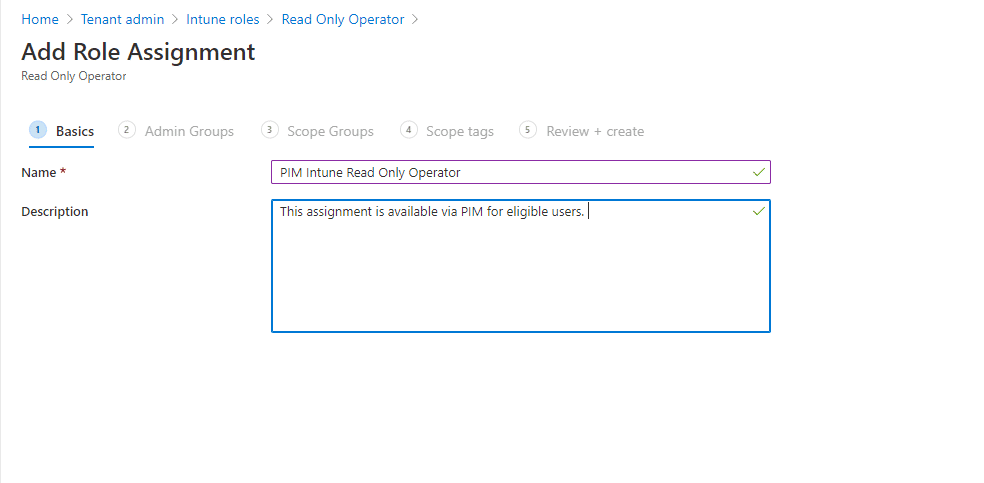
Now we select the corresponding role to the group we created. I am using Read Only Operator as an example. Select the role and click on Assignments – Assign.
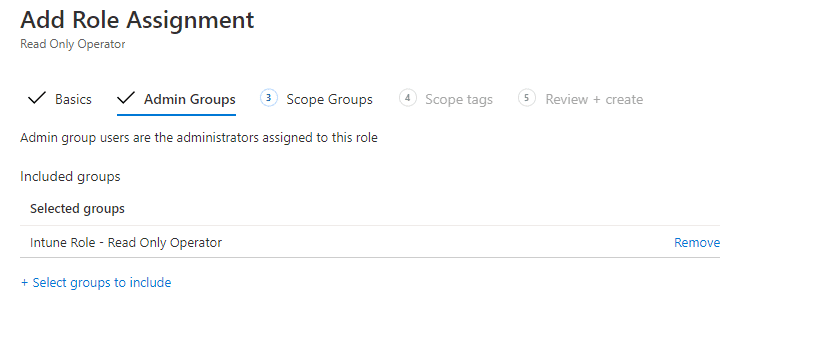
Select the corresponding pim enabled group under the Admin Groups tab.
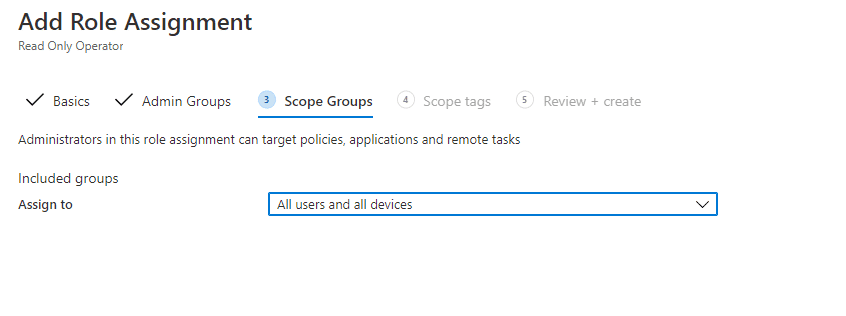
We do want this role to be Read Only for all of Intune, so lets select All Users and Devices under Scope Groups.
I don’t use scope groups, but that could also be used here. For now click Next on the Scope tags tab. On the review and create tab you can verify your settings.
Add your users as Eligible members of the group
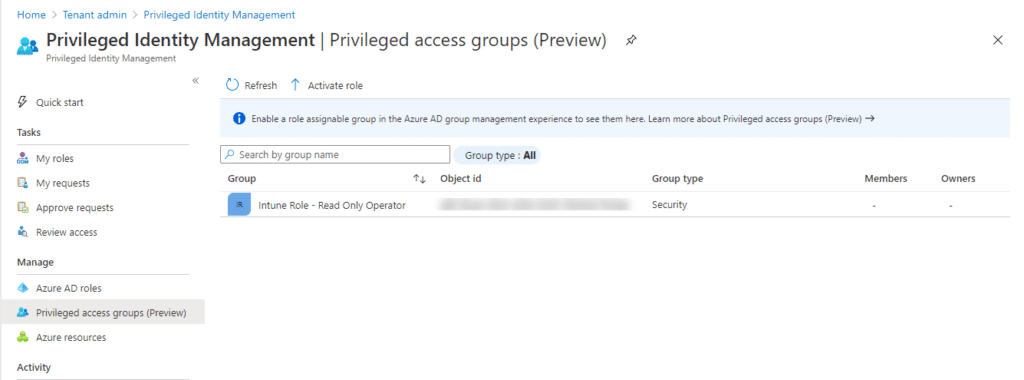
Our group now includes this role and we can assign users to the and they will automatically get the role applied. We are using PIM to assign users as eligible to this group. Go to privileged identity management in the portal. https://endpoint.microsoft.com/#blade/Microsoft_Azure_PIMCommon/CommonMenuBlade/aadgroup
This should now show our group that we created earlier.
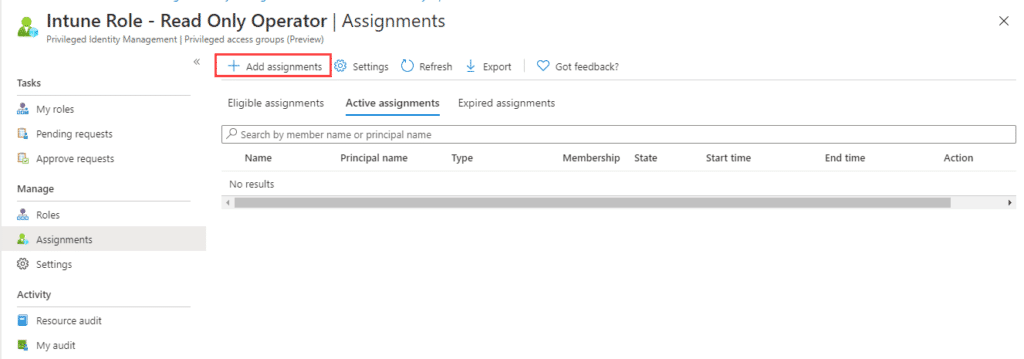
Click on the group to go and go to Assignments.
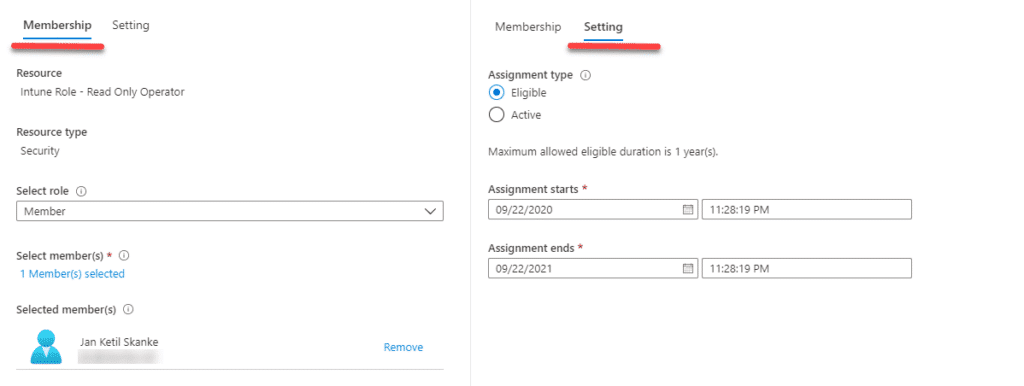
Click on Add assignments and select members you want to add. Check settings to verify it is set to Eligible and not Active. Maximum allowed eligible duration is 1 year.
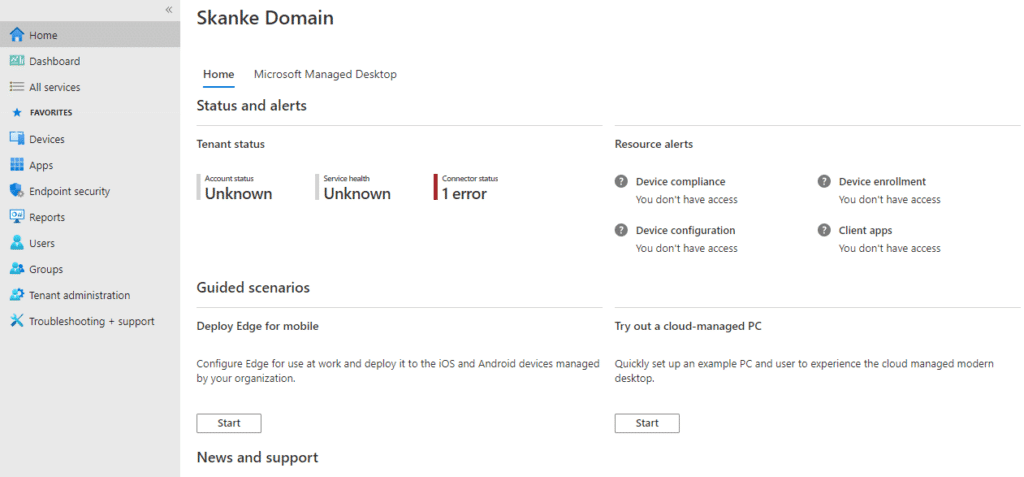
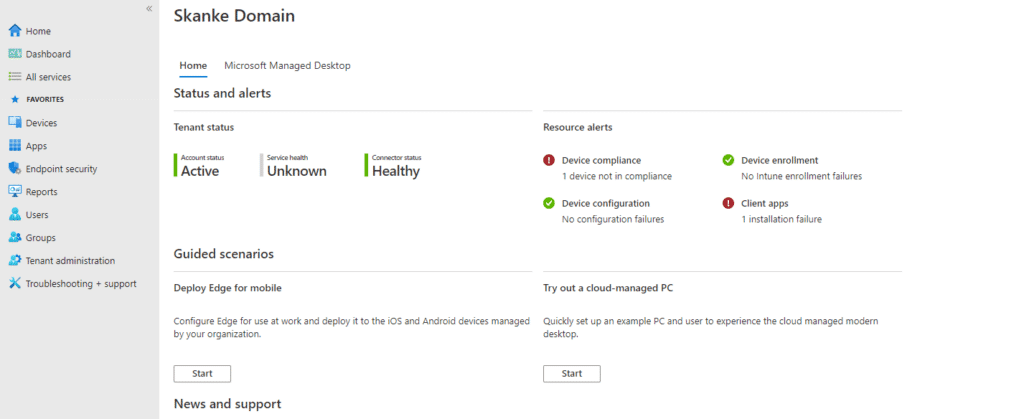
Now the configuration is completed. Lets test this out. Log on to endpoint.microsoft.com with a user you added to the group. The user interface should show that you don’t have access.
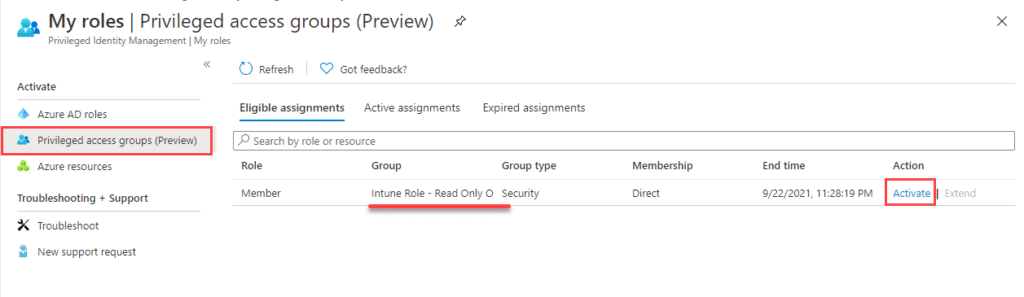
Now go to Tenant Administrator and select Azure AD Privileged Identity Management and click on My roles.
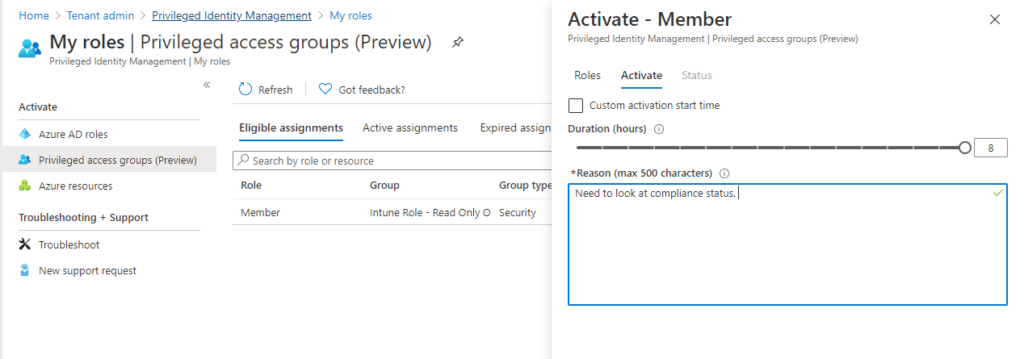
Here you will find Privileged access groups where the user will see what groups is eligible. Click on activate.
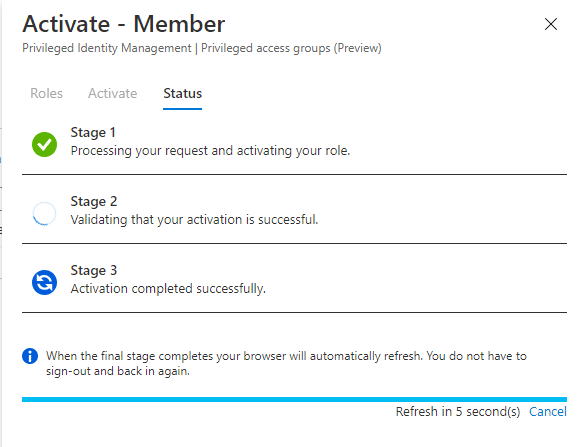
Give a reason for your activation (if configured by your PIM admin) and click on Activate. The activation might take some time to complete and the browser windows will refresh when it is done.
When the process completes the user should be in the group. The user will probably have to log out and log in again to have the role activated in the portal. After logging back in the interface looks like this.
To verify further, go to Tenant Admin – Roles – My Permissions
With this we have PIM capability for the built-in Intune roles. After the current timeslot times out, the user will automatically leave the group and lose the permission/role given. To reactivate, repeat the process.