This article describes how to configure a redundant vpn connection between two fortigate firewalls with two internet connections on one side. This is also known as “route based vpn”. Automatic failover is done by bgp. For bgp to work you need some peering between both firewalls. A standard fortigate vpn tunnel interface does not have an ip address. As such, there is no way to peer between the firewalls.
The process of creating a redundant vpn connection is the same as a standard fortigate to fortigate tunnel. You first have to configure two independant vpn tunnels over the two internet connections. If this is all setup you have to assign tunnel addresses to the vpn interfaces. First you have to check if both tunnels work as expected. When this is the case you can assign tunnel addresses to the unnumbered interfaces. As you can see in the following picture, I used 2 /30 networks.
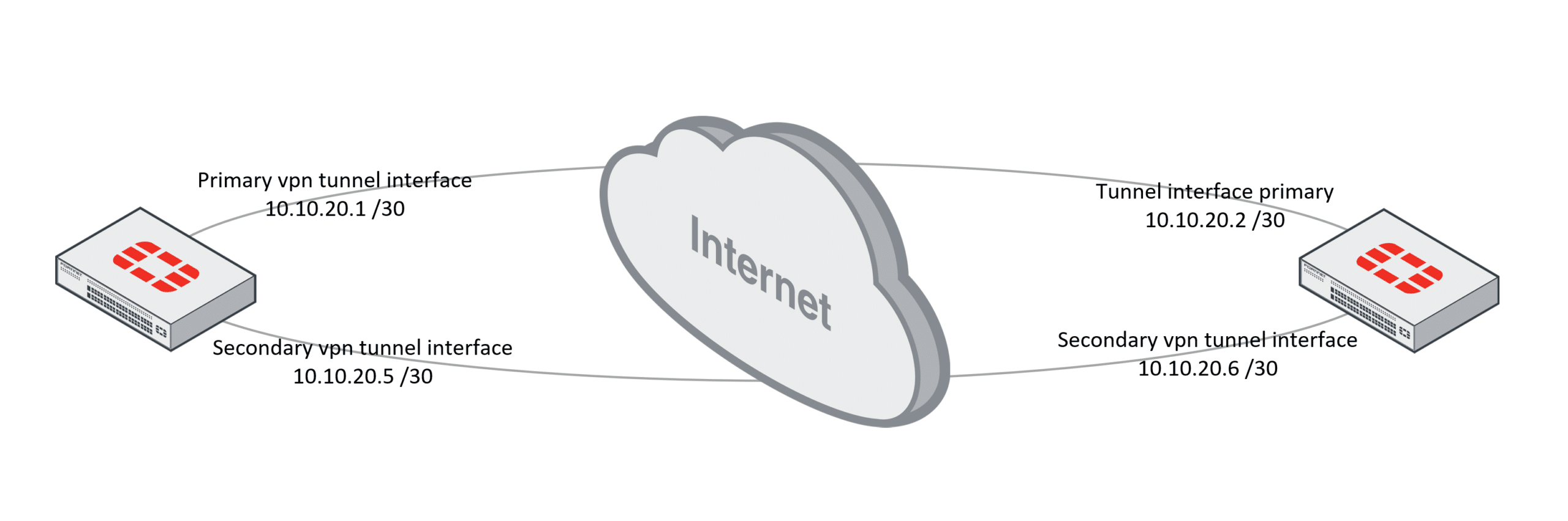
Editing the tunnel addresses
The primary vpn tunnel interface on the left firewall is configured with the following settings:
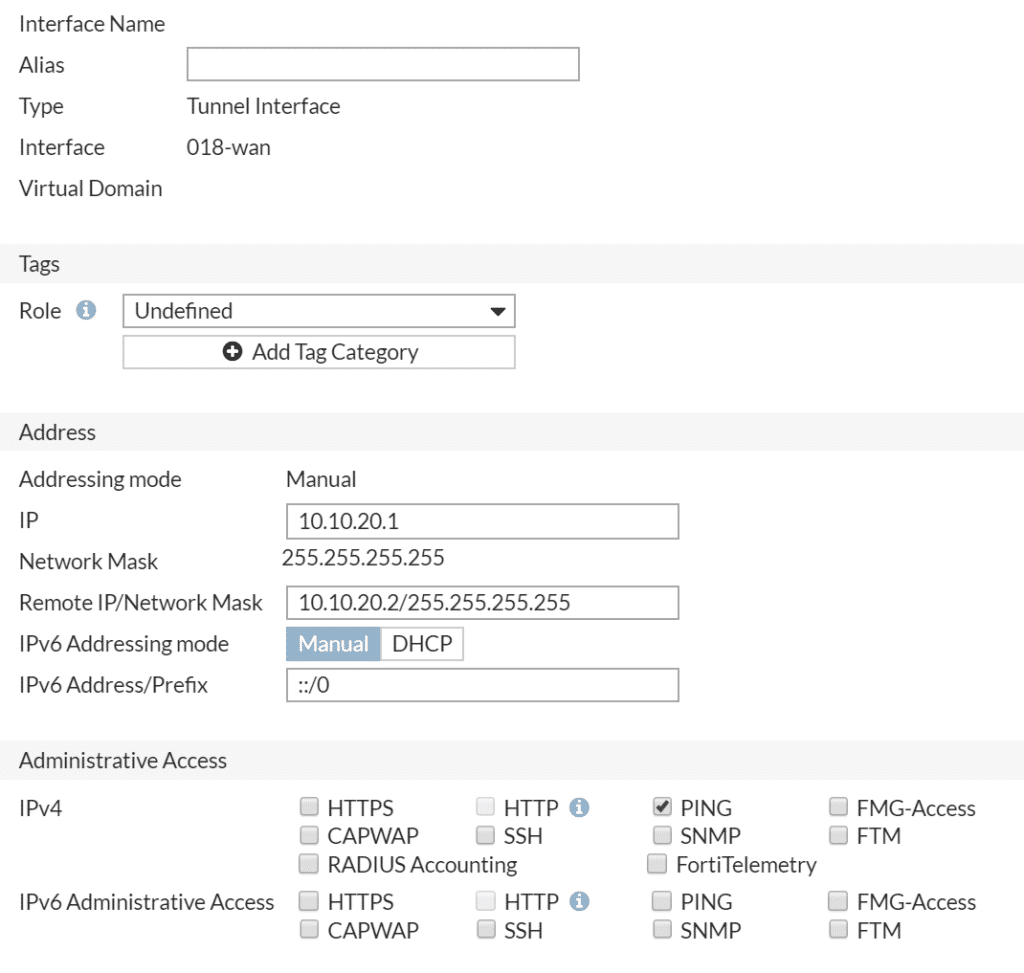
Mention the Remote IP/Network Mask. This has to be the tunnel interface of the firewall on the opposite side. You can configure this with a /32 subnet mask. Configure the other 3 interfaces like this one.
Configuring BGP
You can now proceed with configuring bgp. I choose AS 65018 for this example. Fill in the Local BGP Options as shown in the following picture for the left firewall:
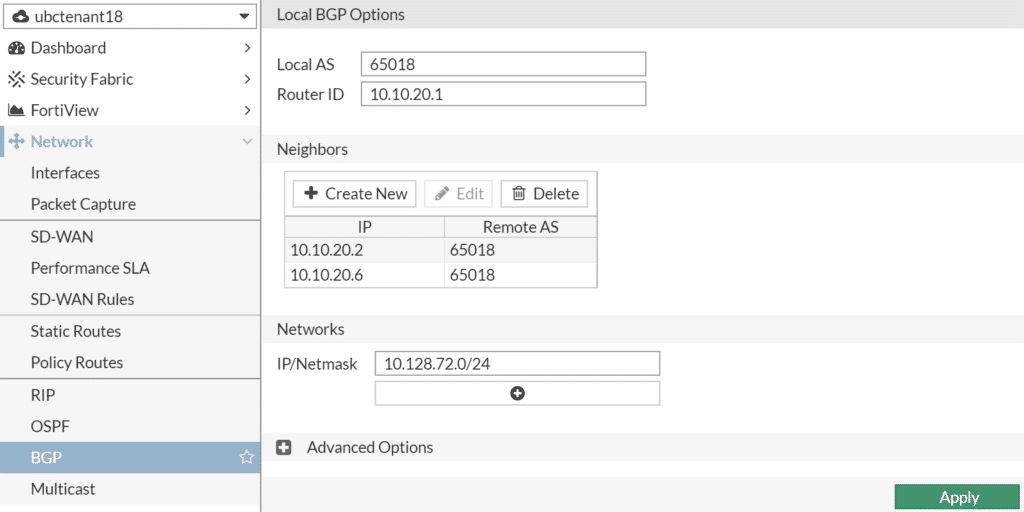
Create the Neighbors, for the left firewall 10.10.20.2 and 10.10.20.6. Add the local networks wich you want to distribute by bgp. In this case 10.128.72.0/24.
Configure the other firewall with the opposite settings. When this is done you have to do some configuration via the cli.
Configuring BGP filters for inbound and outbound routes (cli)
First you have to make some bgp filters for incoming and outgoing routes. This has to be done with route-maps and prefix-lists. First create the prefix list for the local network (left firewall). 10.128.72.0/24 is the local network. 172.16.0.0/12 is the remote network.
config router prefix-list edit "pl-bgp-out" config rule edit 1 set prefix 10.128.72.0 255.255.255.0 unset ge unset le next end next edit "pl-bgp-in" config rule edit 1 set prefix 172.16.0.0 255.240.0.0 unset ge unset le next end next end
Then create the route-maps and assign the prefix-lists:
config router route-map
edit "rm-bgp-out"
config rule
edit 1
set match-ip-address "pl-bgp-out"
next
end
next
edit "rm-bgp-in"
config rule
edit 1
set match-ip-address "pl-bgp-in"
next
end
next
end
Configuring BGP neighbors (cli)
Configure the bgp neighbors via the cli and add the prefix lists to them.
config router bgp
set as 65018
set router-id 10.10.20.1
config neighbor
edit "10.10.20.2"
set next-hop-self enable
set soft-reconfiguration enable
set remote-as 65018
set route-map-in "rm-bgp-in"
set route-map-out "rm-bgp-out"
set weight 200
next
edit "10.10.20.6"
set next-hop-self enable
set soft-reconfiguration enable
set remote-as 65018
set route-map-in "rm-bgp-in"
set route-map-out "rm-bgp-out"
set weight 100
next
end
config network
edit 1
set prefix 10.128.72.0 255.255.255.0
end
config redistribute "connected"
set status enable
end
end
Mention the “set weight” commands. The neighbor with the heighest weight has priority above the one with the one with the lower one. In this case the neighbor with id 10.10.20.2 will take precedence. This finishes the configuration on the left side firewall. You can configure the firewall on the right the same way with opposite settings. When this is done also you setup the vpn with bgp failover succesfully.
Troubleshooting
Both tunnels will always be up because bgp is sending traffic to all of it’s peers. When the tunnels are up and running you need to do some testing. This can be done with the following commands in the cli.
get router info routing-table all get router info bgp neighbor 10.10.20.2 get router info bgp neighbors 10.10.20.2 received-routes get router info bgp neighbors 10.10.20.2 advertised-routes execute route clear bgp ip 10.10.20.2
fill in the corresponding ip addresses with the ip addresses you use. This will give you some output for troubleshooting. Most of the time you will have to correct the prefix lists. Be patient because bgp always needs some time to converge. If you think something is struck you can use the “execute route clear bgp ip <ip-address> command. This reinitializes the bgp session to that peer.