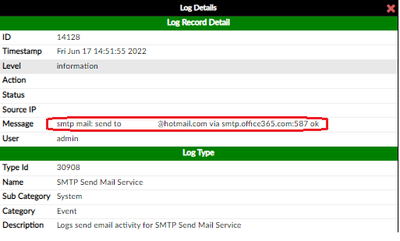
Make sure to enable Authenticated SMTP. You can find this setting at Org settings > Modern authentication.
This article describes how to configure Microsoft Office 365 as a mail server in FortiAuthenticator.
To allow 2FA authentication, configure mail server settings in FortiAuthenticator.
In order to use Microsoft Office 365 mail server, there are some extra steps that need to be configured to allow email from FortiAuthenticator.
FortiAuthenticator is not pre-loaded with Microsoft and other service providers’ certificates, therefore the first step is to add Certificate Chain in FortiAuthenticator as a trusted CAs manually.
Follow the steps mentioned below to download and import the certificate in FortiAuthenticator before starting to configure email settings.
To get the certificate of Microsoft Office 365.
1) Download and install OpenSSL on any Windows machine.
2) Navigate to the OpenSSL directory and execute this command.
In this example, OpenSSL is installed in C:\.
– Ensure that the right directory is used to execute this command.
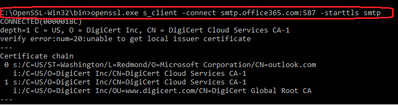
3) C:\OpenSSL-Win32\bin> openssl.exe s_client -connect smtp.office365.com:587 -starttls smtp
CONNECTED(0000018C)
depth=1 C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
verify error:num=20:unable to get local issuer certificate
—
Certificate chain
0 s:/C=US/ST=Washington/L=Redmond/O=Microsoft Corporation/CN=outlook.com
i:/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
1 s:/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
i:/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA
—
Server certificate
—–BEGIN CERTIFICATE—–
MIIIpDCCB4ygAwIBAgIQCKADw/Or6WqnCIVhHvaGQjANBgkqhkiG9w0BAQsFADBL
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMSUwIwYDVQQDExxE
aWdpQ2VydCBDbG91ZCBTZXJ2aWNlcyBDQS0xMB4XDTIxMTIyMjAwMDAwMFoXDTIy
MTIyMjIzNTk1OVowajELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24x
EDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlv
bjEUMBIGA1UEAxMLb3V0bG9vay5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAw
ggEKAoIBAQCx8iKoaXhfNV7nuguyQXV8YrfJ0IPCtmppi1ll+5CgQPEcd9K8v0le
bOsMHwYFwSzmqWorZVWtm8VSbJB+ZKZrmsbbPhVOjqRUMeb77YwA6h4DzZV3rWC3
WopQBzO1DANeNF7RuF+sjikXzD+TWFPsPuqEJjZRYFo+cDfsYwFB95tPYkQ61S4p
1JA6cwpYnCuCSqXGEavRoQ6e6YDMQYNXXAoWs7Nr0VOCtYJV/pOWtCZqHzsYydzG
J/sqVaXuDYf+HjFL/tha94vGnWLgAITdqZorMKi/sSQ3dd63SIWfwJnKYD85R2cR
GTW+LZY4Up8FsSb9yKhYxi494e3Thj3VAgMBAAGjggVjMIIFXzAfBgNVHSMEGDAW
gBTdUdCiMXOpc66PtAF+XYxXy5/w9zAdBgNVHQ4EFgQUC662b5wqMtyvz2nhIYV0
oqnG/jMwggIQBgNVHREEggIHMIICA4IWKi5pbnRlcm5hbC5vdXRsb29rLmNvbYIN
Ki5vdXRsb29rLmNvbYILb3V0bG9vay5jb22CDW9mZmljZTM2NS5jb22CDyoub2Zm
aWNlMzY1LmNvbYIXKi5vdXRsb29rLm9mZmljZTM2NS5jb22CDCoub2ZmaWNlLmNv
bYISb3V0bG9vay5vZmZpY2UuY29tghRzdWJzdHJhdGUub2ZmaWNlLmNvbYIbYXR0
YWNobWVudC5vdXRsb29rLmxpdmUubmV0gh1hdHRhY2htZW50Lm91dGxvb2sub2Zm
aWNlLm5ldIIgYXR0YWNobWVudC5vdXRsb29rLm9mZmljZXBwZS5uZXSCFmF0dGFj
aG1lbnRzLm9mZmljZS5uZXSCFiouY2xvLmZvb3RwcmludGRucy5jb22CFioubnJi
LmZvb3RwcmludGRucy5jb22CHWNjcy5sb2dpbi5taWNyb3NvZnRvbmxpbmUuY29t
giFjY3Mtc2RmLmxvZ2luLm1pY3Jvc29mdG9ubGluZS5jb22CGHN1YnN0cmF0ZS1z
ZGYub2ZmaWNlLmNvbYIaYXR0YWNobWVudHMtc2RmLm9mZmljZS5uZXSCCioubGl2
ZS5jb22CFm1haWwuc2VydmljZXMubGl2ZS5jb22CC2hvdG1haWwuY29tgg0qLmhv
dG1haWwuY29tMA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYI
KwYBBQUHAwIwgY0GA1UdHwSBhTCBgjA/oD2gO4Y5aHR0cDovL2NybDMuZGlnaWNl
cnQuY29tL0RpZ2lDZXJ0Q2xvdWRTZXJ2aWNlc0NBLTEtZzEuY3JsMD+gPaA7hjlo
dHRwOi8vY3JsNC5kaWdpY2VydC5jb20vRGlnaUNlcnRDbG91ZFNlcnZpY2VzQ0Et
MS1nMS5jcmwwPgYDVR0gBDcwNTAzBgZngQwBAgIwKTAnBggrBgEFBQcCARYbaHR0
cDovL3d3dy5kaWdpY2VydC5jb20vQ1BTMHwGCCsGAQUFBwEBBHAwbjAlBggrBgEF
BQcwAYYZaHR0cDovL29jc3B4LmRpZ2ljZXJ0LmNvbTBFBggrBgEFBQcwAoY5aHR0
cDovL2NhY2VydHMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0Q2xvdWRTZXJ2aWNlc0NB
LTEuY3J0MAwGA1UdEwEB/wQCMAAwggF8BgorBgEEAdZ5AgQCBIIBbASCAWgBZgB1
ACl5vvCeOTkh8FZzn2Old+W+V32cYAr4+U1dJlwlXceEAAABfd92KNcAAAQDAEYw
RAIgK1OoayOTzmZhLBTA59kK4wDo6wrIN6cqkQF5aq+RRkoCID9wliAcCpH5/xuw
lbXhD802mYt6rTvhE28q46XI+JxMAHUAUaOw9f0BeZxWbbg3eI8MpHrMGyfL956I
QpoN/tSLBeUAAAF933Yo2QAABAMARjBEAiATdes8mfBPe7c6Jr5ugzsah+pL1exf
DS52v3nrer6BzAIgR+3KS+FiwwaHUGHSxN590BgyM+tpWTvXKO+Bew9E3LcAdgBB
yMqx3yJGShDGoToJQodeTjGLGwPr60vHaPCQYpYG9gAAAX3fdih4AAAEAwBHMEUC
IQDlJfrDDM9dqLit2DyDbU2DHQ4s1KFC0RVLDhbgH/SV2gIgW2ruP4ypX4uzJLVI
DNUycp/X622bLayb8GOPeR+W0uAwDQYJKoZIhvcNAQELBQADggEBAF8Sg/U5PslL
xTvAa8fZDOomCB1vTbeW/0Hdhoo5GQqhavcKNpmlFMmIac5PsFnld/wAKrplyt6H
OsJsO6iHnZG5FhoMlsSUAMyApcwPQS3kD9+zq15fjtWBPs2EGQE9cF8Y4MkRhL4g
kRlKqlcDs+Rs0pOAqzAcro9AO0VNIWtmmNhp5TBnoDIBoY5NOHwYaSairNlpE51B
YEQJrXhJqcLHT+pDyqr8UdT/LE2qRRQCWcsM7gzu/AFJcJIbfl/lmX3DHJV/CmXP
GkB/ICCFVD4qk2+OfaQk/QlZpGIokfiIlsVmVR8ik+z/v5A4XmYDOxrD0gY2DLYF
HqZj57jM5ME=
—–END CERTIFICATE—–
subject=/C=US/ST=Washington/L=Redmond/O=Microsoft Corporation/CN=outlook.com
issuer=/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
—
No client certificate CA names sent
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: 0x04+0x08:0x05+0x08:0x06+0x08:RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:
ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Shared Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:
ECDSA+SHA512
Peer signing digest: SHA256
Server Temp Key: ECDH, P-384, 384 bits
—
SSL handshake has read 4379 bytes and written 379 bytes
Verification error: unable to get local issuer certificate
—
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 7C0000005C44F21989E7A7385F296969267B7E51E2AF383CBF7AF8FCB88E3BD9
Session-ID-ctx:
Master-Key: F64BF52AA75F4CD9E331D6F84E4AB38A0218D628D677442707877B90D1EDFB495C2726B
B284FDBF20DD58CEB7D7EAAE9
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1655461985
Timeout : 7200 (sec)
Verify return code: 20 (unable to get local issuer certificate)
Extended master secret: yes
—
250 SMTPUTF8
451 4.7.0 Timeout waiting for client input [AS9PR06CA0739.eurprd06.prod.outlook.com]
read:errno=0
4) Copy and Paste from ‘—–BEGIN CERTIFICATE—–’ to ‘—–END CERTIFICATE—–’ including ‘—‘ signs to notepad and save the file as .CER extension.

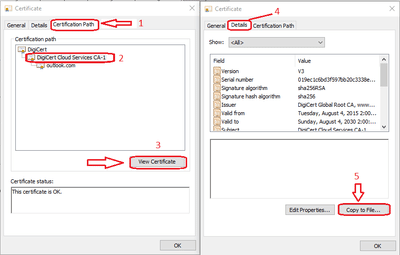
5) Open the Certificate file, which is just created in the above step and select the ‘Certification Path’.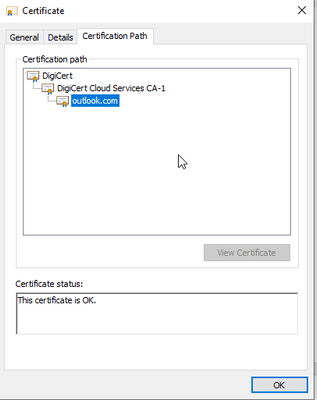
Export Intermediate Certificate.
6) Now from here select the Intermediate certificate, in this case, ‘DigiCert Cloud Services CA-1’. Export the certificate and save it.
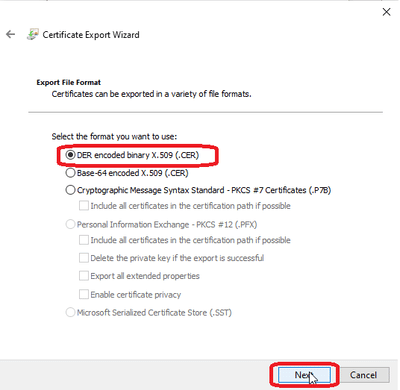
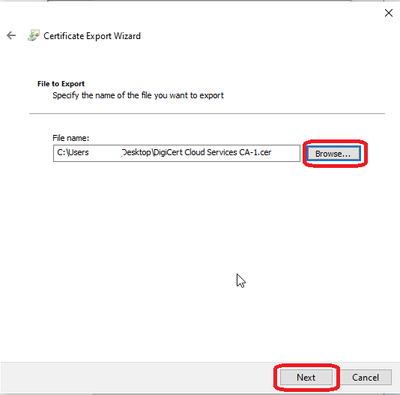
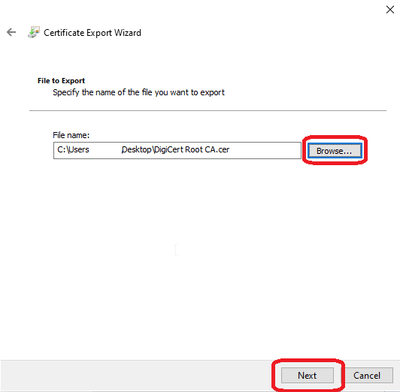
Select Browse and save this Certificate file.
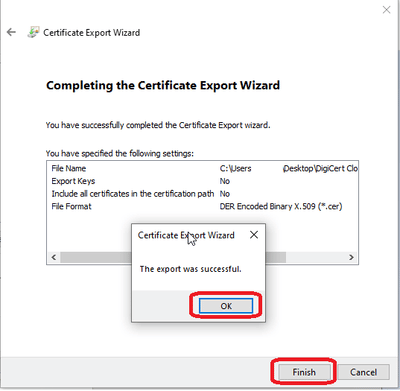
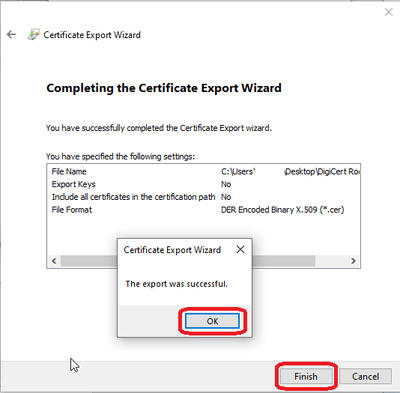
Select Finish to complete the Export Wizard and then select OK to complete.
Export Root Certificate.
7) Now from here select the Root Certificate, in this case, ‘DigiCert Cloud Services CA-1’. Export the certificate and save it.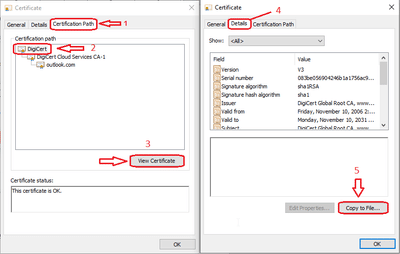
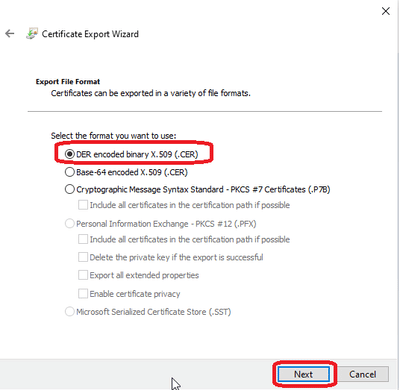
Select Browse and save this Root Certificate file.
8 ) Import these Root and Intermediate Certificates to Trusted CAs in FortiAuthenticator.
Logon to FortiAuthenticator and navigate to Certificate Management -> Certificate Authorities ->Trusted CAs -> Select Import to add both Root and Intermediate CAs and select OK.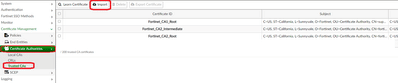
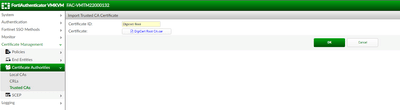
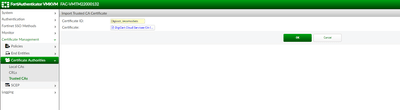
Once both Root and Intermediate CAs are imported. The Trusted CAs list can be seen.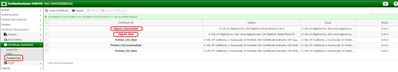
9) In the FortiAuthenticator go to System -> Messaging -> SMTP Servers and select Create New.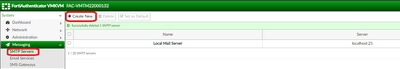
10) Create a new SMTP Server, fill out the required information. Ensure to select STARTTLS.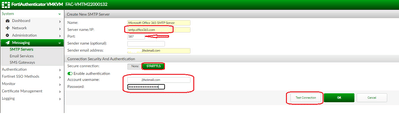
11) Select Test Connection.
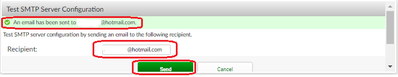
12) Check the FortiAuthenticator Logs. Go to Logging ->Logs.